Cryptographically Secure Voting
- Home
- Cryptographically Secure Voting
As our world becomes ever more immersed in technology, it’s clear that voting online in elections is something that is bound to happen in the future. However, there are some questions that remain, such as “WHEN will it be implemented?”, “HOW will the voters’ privacy be protected?”, and “HOW will the system be secured?”
The time for online voting is now, which can be done privately and securely, the Follow My Vote way.
The Follow My Vote online voting platform uses elliptic curve cryptography to secure its operations. For more information on cryptography and how we use it, please visit our page on Elliptic Curve Cryptography & Securing Online Voting.
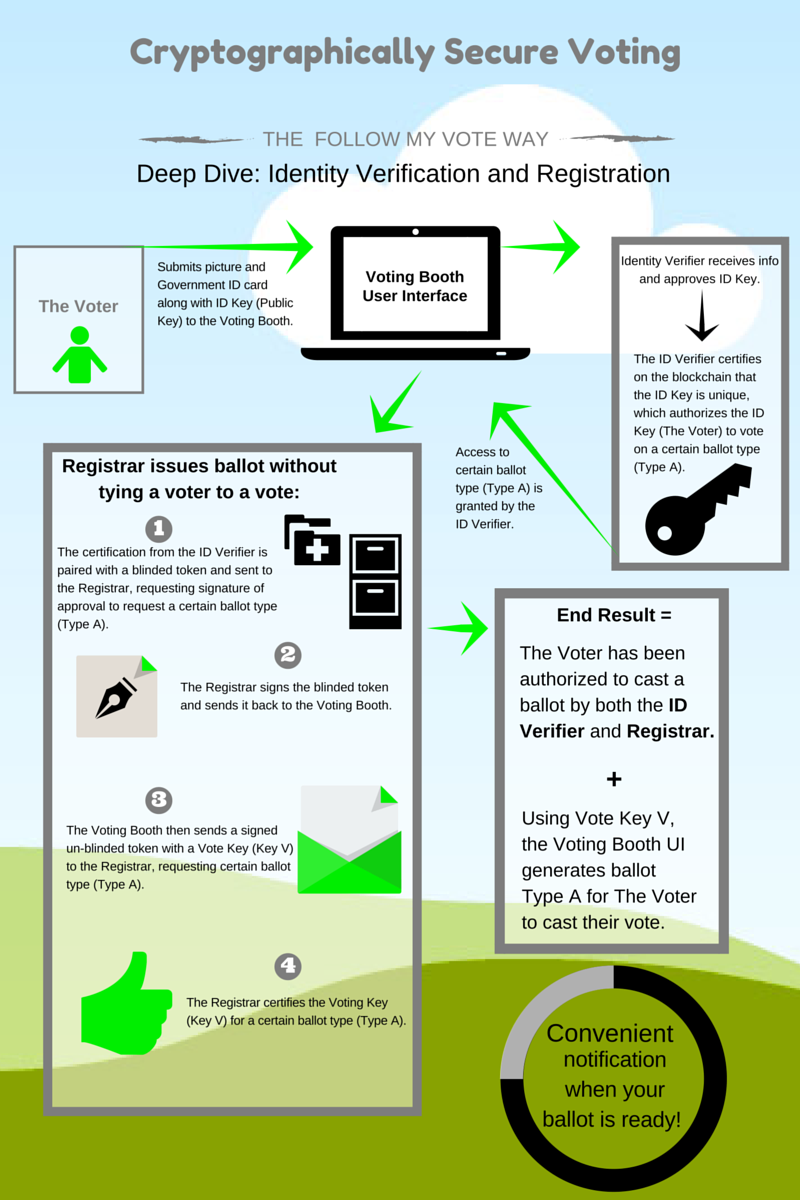
To help further explain, we’ve created this infographic to explain how the system operates using a cryptographically secure voting process to ensure that each voter is issued the correct ballot without their identity being tied to their vote(s).
To summarize the above infographic, in Follow My Vote’s online open-source voting system, a voter must have their identity verified by an Identity Verifier and be issued a ballot by the Registrar. The Identity Verifier reviews the voter’s personal information, certifies that the voter’s identity hasn’t already been registered within the system, determines which ballot type the voter is supposed to receive, and ensures that the voter is only authorized to request one ballot in each election. The Registrars are responsible for preparing the ballot types and ensuring that each voter is issued the correct ballot type.
The beauty of our online voting system’s design is that the Identity Verifier will never know how each voter has voted on their ballot; and, the Registrar will never know the identity of the voter they issue the ballot to, which ensures that each voter’s right to privacy is protected when casting their ballot.
To learn more about how our voting system works as a whole, please visit our page on Blockchain Voting: The End To End Process.


Comments (6)
Jay Stewart
2016-09-03Is there a charge to vote via the Bitshares blockchain? If so, what would the charge be?
Will Long
2016-09-30Jay, Yes there are blockchain fees to add new transactions to the BitShares blockchain. You can view the fee schedule here: https://cryptofresh.com/fees
Tom
2016-10-07Consider this type of voter registartion fraud: Alice steals Bob’s identity and registers Bob to vote with the Registrar. Later, Bob tries to register to vote but is denied because it appears he has already registered. How do you invalidate Bob’s fraudulent Vote Key and issue him a new one?
Also, how can voters be sure that key generation is truly random, and no rouge agent can predict or “easily” guess the keys that the Registrar or Voting Booth are using to sign messages?
Samir Moussallem
2017-01-09Dear Sir,
i have requirement for voteing soluation software, please send me more details and cost.
thanks for your support
Regards.
Samir
Tessie
2017-03-10Kndloewge wants to be free, just like these articles!
Will Ralphs
2017-01-20I’m stoked to see you guys working on such a well targeted project.. this is exactly what we need!
I am curious how the ‘verifier’ is selected. The best solution I could think of for verifier’s would be for any verified user to be able to act as one, and then each verifier only receives segments of the data; the last 4 of the drivers license, and every 3rd letter of the name for example, and certain sections of the photo go to each verifier, so that no verifier ever receives a complete image of a person, or any other complete or useful information.
I would think 8 verifier’s per submission on an active system would make sense; even if the verification needs to wait overnight for 8 to be available.
It would be important that verifier selection did not occur at the time of the vote, as that could result in an organization getting all their users online to act as verifiers, and then they could authenticate fraudulent accounts.
I think doing the verification in a manner similar to RAID would be the cleanest solution, assuming you have the user base. (e.g. send redundant data to additional users both to improve security, and speed/reliability.)
Fascinated to learn more about your project!