The Future of Voting
- Home
- The Future of Voting


Recently, the U.S. Vote Foundation, with funding from the Democracy Fund, released the findings of a comprehensive study that evaluated the feasibility of electronic voting from cybersecurity, political, and social perspectives. The project focused exclusively on technologies which are end-to-end verifiable, meaning simply that voters can verify that their own votes have been recorded accurately and that all votes were tallied correctly. Here we will summarize the goals, methodologies, and findings of the E2E-VIV project.
Project Team
The project team consisted of a diverse group of technologists, computer scientists, and election officials, who were broken into the sub-teams of technical, usability, testing, and local election officials. Galois, a technical and research consultant firm, provided engineering and technical project management
The project also gathered input from essential project stakeholders, such as election verification advocates, standards bodies such as the Institute of Electrical and Electronics Engineers (IEEE), election systems vendors, hackers and hacktivists, election officials, and voters.
Evaluation of Current System
The team identified several weaknesses of current voting processes, including:
- Voters with disabilities cannot vote without assistance
- Communication with remote voters is slow and unreliable
- Vote tallying is both labor-intensive and prone to error
- Audits of elections are costly
- The process offers little transparency, and voters must implicitly trust election officials and hardware vendors
Required Properties of E2E-VIV Systems
The specifications of an end-to-end verifiable voting system were divided into the categories of technical and non-functional. Technical requirements were identified as those that can be addressed by the design and implementation of the system, such as user authentication. The non-functional requirements are those where the system depends on external behaviors, such as election certification guidelines.
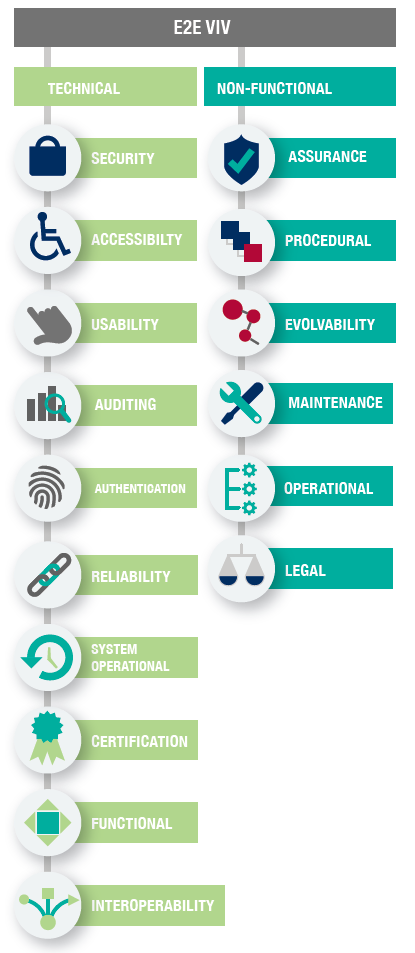
Technical requirements
Functional
For each ballot cast there must be a corresponding voter. The connection between the voter and the ballot must be maintained only until the end of the election, especially in the case that voters are allowed to change their votes by resubmitting their ballots. However, the system must simultaneously be able to maintain complete voter anonymity and upon the close of the election there should be no way to connect voters to their ballots.
Security and Authentication
Data must be retained in spite of system irregularities and failures. The system must also ensure the integrity of sensitive information such as lists of registered voters and ballots. This must hold true even if the individual voter’s device contains malicious code.
By way of authentication, the system must be able to recognize individual voters so that no voter is mistaken for another. Individual voters should not be able to waive their right to privacy. Only eligible voters must be allowed to cast ballots.
Individual authentication codes and passwords should be changed at least once per election cycle and at the request of the voter or the election official.
Vote tabulation should be strongly software independent such that any compromise in the tallying of ballots can be detected; if a compromise is detected, the data needed to reconstruct the tally must be available.
Usability
An E2E-VIV system should be easy to use, as user experience is critical to widespread adoption of the system.
Accessibility
Voters with disabilities should be able to easily use an E2E-VIV system.
System Operational
These requirements ensure that election officials configure, update, and run the system in a transparent way. Logs should be collected and published of all system details, and all changes should be correctly and promptly documented. Equipment should be kept in a safe and protected area. Officials should have documented contingency plans for possible system failures. Any backup systems should also be properly maintained as according to documented protocol.
Interoperability
No proprietary data or communication standards should be used. Developers should use the Election Markup Language for data interchange and configuration.
Auditing
An E2E-VIV voting platform should have auditing capabilities built into the original system, and not as an afterthought. It must record data such as the number of eligible voters, the number of votes cast, count results, any detected attacks on the system, and any system failures. To be truly auditable, the system must be open source and the code must be published in full.
Reliability
An E2E-VIV system should be able to run continuously and handle the expected volume of voters. It should be available at all times during the election period, and should be able to recover from failures in less than 10 minutes. Network configuration should be able to withstand repeated denial of service attacks, and should be revamped every election cycle to stay abreast of evolving attack technologies.
Certification
Tests should be designed that can provide evidence for certification for each functional requirement and should be easily understood and run.
Non-Functional Requirements
Operational
This requirement is comprised of several sub-categories: voter assistance, election and registration timing, voter registration, candidate nominations and lists, receipt freedom, election integrity, and openness.
Voter assistance requirements demand that election officials inform voters in clear and simple language how elections will be organized and administered, and how they should participate. This includes clearly communicating necessary software and hardware, including configuration options to increase security.
Voter registration requires that officials plan and communicate the periods during which voters may cast their ballots.
Voter registration requirements mean that the system must allow voters to check that their information is correctly recorded and request any correction. The list of registered voters should be updated regularly by election officials.
Candidate nominations and lists require that the ballot itself be free of any fonts, sizes, styles, or other embellishments that may consciously or unconsciously lead a voter to prefer a specific candidate.
Receipt freedom requires that privacy and security remain intact even if a person were to photograph, screenshot, or videotape any part of the election process.
Election integrity requires that any tests of the voting system are clearly communicated as tests, and that results are never disclosed to anyone until the close of the election period.
Openness demands that a deployed E2E-VII system functions correctly despite having large parts of the system, i.e. client hardware and software, unknown, unsecured, uncertified, and out of the control of election officials.
Procedural
Procedures must be developed relating to provisioning, certification, maintenance, availability, and use. These procedures must be made available to the public. After the system is introduced, officials must actively develop the voters’ trust. Additionally, clear technical and legal procedures should be established that outline a path forward in the case that voters can prove that their votes were not accurately received or counted.
Legal
Unless the internet and thus online voting is universally available, they must only be used as an additional means of voting and not to replace traditional means of voting. The legal requirement involves other specifications regarding accessibility and availability.
Assurance
There are several assurance requirements related to the implementation, documentation, and licensing of end-to-end verifiable voting systems. Client software must exhibit strong security with respect to voter authentication. All aspects of the design, architecture, algorithms, and documentation for the system should be published and available for free download. All documentation should be continually updated. The source code and related development information should similarly be available for free download and inspection under a license that permits anyone to download, build, instrument, and test the system.
Maintenance and Evolvability
Election officials, or any entity selected by the election officials, must have the rights and ability to update the system to conform to changes in law, technology, or threats to system integrity independent of the original vendors of the system. They must also have the right and ability to correct system flaws.
Recommendations
1. Any public elections conducted over the internet must be end-to-end verifiable.
2. No Internet voting system of any kind should be used for public elections before end-to-end verifiable in-person voting systems have been widely deployed and experience has been gained from their use.
3. End-to-end verifiable systems must be designed, constructed, verified, certified, operated, and supported as high-assurance systems according to the most rigorous engineering requirements on mission and safety-critical systems.
4. E2E-VIV systems must be usable and accessible.
5. Many challenges remain in building a usable, reliable, and secure E2E-VIV system. THey must be overcome before using Internet voting in public elections. Research and development efforts toward overcoming those challenges should continue.

