Voting System Vulnerabilities
- Home
- Voting System Vulnerabilities
We have reviewed the top voting system companies and compiled a list of their most notable voting machines that have vulnerabilities. In some cases the faulty voting machines were used for several years before an elected official decided to decertify the machines.
WinVote

On April 14, 2015, Virginia Governor Terry McAuliffe decertified the WinVote electronic voting machines. Jeremy Epstein, a senior computer scientist at SRI International, broke down the Voting Equipment Report that revealed the many concerns with the WinVote system, namely its complete and utter vulnerability to even the most basic of hackers.
These vulnerabilities are nothing new, and can be traced back to when electronic voting was first allowed into the election process in 1990 by the Federal Election Committee. This newest report finally brought about the decertification of a system already tossed aside by both Pennsylvania and Mississippi. These machines, purchased from a vendor that went out of business five years ago, were used in 30 localities in Virginia.
According to the report, the machines’ encryption codes were as simple as ‘abcde’ and ‘admin.’ The machines themselves were nothing more than laptops embedded with Windows XP, with physical ports that made physical attacks laughably easy. In addition, the systems hadn’t been patched in more than 10 years. Epstein posited that a person within a half-mile of the voting center could hack into the machines and change votes completely undetected.
Diebold

Hackable electronic voting machines are not new headlines for the United States. In 2011, a team of Princeton computer scientists hacked Diebold machines in seven minutes. The “man-in-the-middle” attack consisted of a person picking the lock on the external port of a machine and inserting “alien electronics”. “Indeed, the Argonne team’s attack required no modification, reprogramming, or even knowledge, of the voting machine’s proprietary source code,” said Salon writer Brad Friedman.
Friedman went on to quote the leader of the assessment team Roger Johnston. “We believe these man-in-the-middle attacks are potentially possible on a wide variety of electronic voting machines. We think we can do similar things on pretty much every electronic voting machine.”
Sequoia

Between 2007 and 2009, Sequoia Voting Systems made news when Princeton computer scientists, and later University of California computer scientists, found enough exploitable vulnerabilities to prove it was possible to change the outcome of an election without detection.
In 2007, after New Jersey requested the Princeton team’s attention, Sequoia actually threatened the Princeton Computer Scientists with legal action if they continued with their assessment. New Jersey would later release the report and decertify Sequoia in that state. According to VerifiableVoting.com, Sequoia machines suffer from ineffective safeguards against data tampering, easily circumvented cryptography permanently hardwired into the machines, and numerous programming errors.
The Sequoia machines are still used in six states by at least nine million voters, only now Sequoia is owned by Dominion Voting Systems.
ES&S
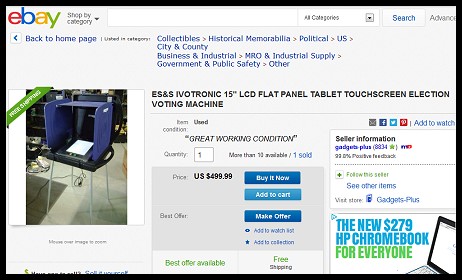
In a concerning turn of events, Election Systems and Software (ES&S) is currently selling their used but “IN GREAT CONDITION” iVotronic machines on EBAY. The iVotronic is currently the most widely used electronic voting system in the country. Interestingly, the iVotronic has been the machine used in some of the most questionable elections in the last 10 years.
Hart InterCivic

Hart Intercivic machines were tested in the summer of 2007 by the Pennsylvania State University academic team, building upon past studies. The State of Ohio commissioned the study which was called the EVEREST study and found some surprising results.
There were four evaluation results stemming from the study that applied to all machines tested:
- Failure to effectively protect election data integrity
- Failure to protect an election from malicious insiders
- Failure to provide trustworthy auditing
- Unsafe features and practices
Other discoveries surrounding Hart machines included:
- There is a veritable sea of previously undetected functionality in the Hart system. Note that we found what we believe is only a tiny fraction of the features enabled through undocumented software triggers, e.g., Windows registry entries.
- An attacker may subvert all back-end data protections in the Hart and Premier systems by exploiting combinations of new and previously known vulnerabilities.
- It is possible to replace Hart system firmware in seconds with unfettered access to the equipment.
Premier Election Solutions (Formerly Diebold, Now owned by Dominion Voting Systems)

Premier Election Solutions machines were also included in the Everest Study. The four evaluation results from the study remain true for Premier.
Additionally, The study concluded:
- The Premier EMP (memory card encoder) and VCE (voter token encoder) system components are vulnerable to a large number of previously unknown attacks that if exploited can undermine the entirety of the election process.
- There exist critical failures in the previously unstudied Verdasys Digital Guardian security software. This software is used by the state of Ohio to defend the Premier GEMS server upon which the back-end election processes are based.
The Take-away
Several things can be learned from these system failures. First, the machines must be physically sound. Second, the programming must not have holes that can be exploited. Third, it’s not best practice to have extremely simple and guessable passwords hardwired into a voting machine.