
Follow My Vote Releases Patent-Pending IP As A Gift To Humanity
Today marks the dawn of a new era, the day we at Follow My Vote release our Intellectual Property (IP) covering our patent-pending architecture for a secure end-to-end verifiable blockchain-based voting system capable of securely hosting honest elections with mathematically provable results.
We’ve come to a point in human history where faith in the democratic process has reached all-time lows, especially here in the United States. At Follow My Vote, we believe there is still hope for humanity in this regard.
Ever since we inked our patent pending designs back in 2014, we’ve had aspirations to bring our designs to life, enabling citizen’s throughout the world to cast their votes with integrity on Election Day. However, taking on such a massive endeavor comes with it’s own set of challenges.
We have learned and accomplished a tremendous amount at Follow My Vote over the years, while trying to bring our vision to life. Throughout this time period, we’ve seen various new voting systems come and go, all claiming to be better than the last. However, when analyzing these systems we’ve detected issues that need to be addressed before being implemented on a mass scale. Despite these issues, some of these solutions are actually gaining traction, which is also concerning to us at Follow My Vote.
We’ve seen widespread infighting in the voting space over the years, mainly between those that are all for adopting modern technology where possible to improve the political process for everyone involved vs those that don’t. We have technology providers developing and testing solutions, while university researchers speak out against their efforts and shine light on the vulnerabilities that exist with these solutions. There has been so much back and forth over the years and a lot of misinformation being thrown around that, as a result, it’s almost as if the majority of people have become convinced that technology cannot save us. We simply disagree.
With this in mind, we are releasing this IP today, as a gift to humanity, in hopes to restart the conversation when it comes to question: “Can ‘We the People’ figure out a way to securely conduct verifiable elections online?”
Let’s be real. If you could vote conveniently from your smartphone on Election Day and be reassured by the world-wide technological community at large that your vote was cast as intended and counted as cast, wouldn’t you? That’s what we are really striving for at Follow My Vote.
From Follow My Vote’s perspective we’ve already designed the voting system that, once developed, will have the upmost integrity in existence. Just keep in mind, it’s going to take us some time to bring it to life.
In the meantime, we encourage you to closely review our patent application as published on Google Patents and get involved in the conversation.
Upon review of our patent application, we’d like to immediately draw your attention to the figures or drawings, Figure 1 and Figure 2.
Figure 1, as shown below, is simply a list of key components that exist within our voting system design.
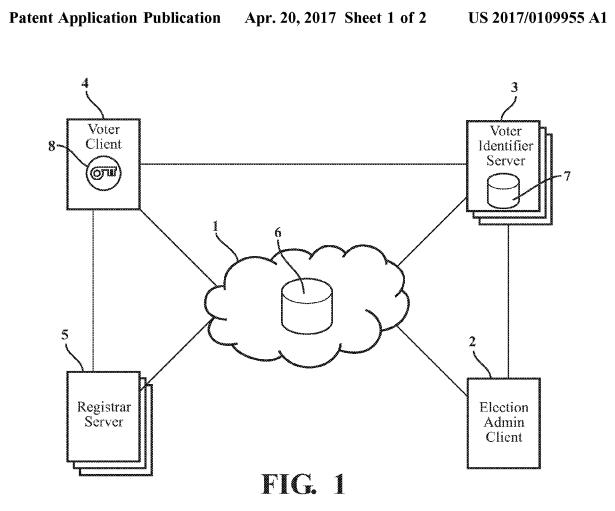
Figure 2, as shown below, showcases our (once patent-pending / now open-source) anonymous voting key registration protocol, which enables someone to have their identity verified for voter eligibility and subsequently be granted access to their eligible election contests in an anonymous way so that, when they cast their votes, they will be able to literally follow their vote(s) into the blockchain-based ballot box and confirm with their own eyes that their vote was cast as intended and counted as cast.
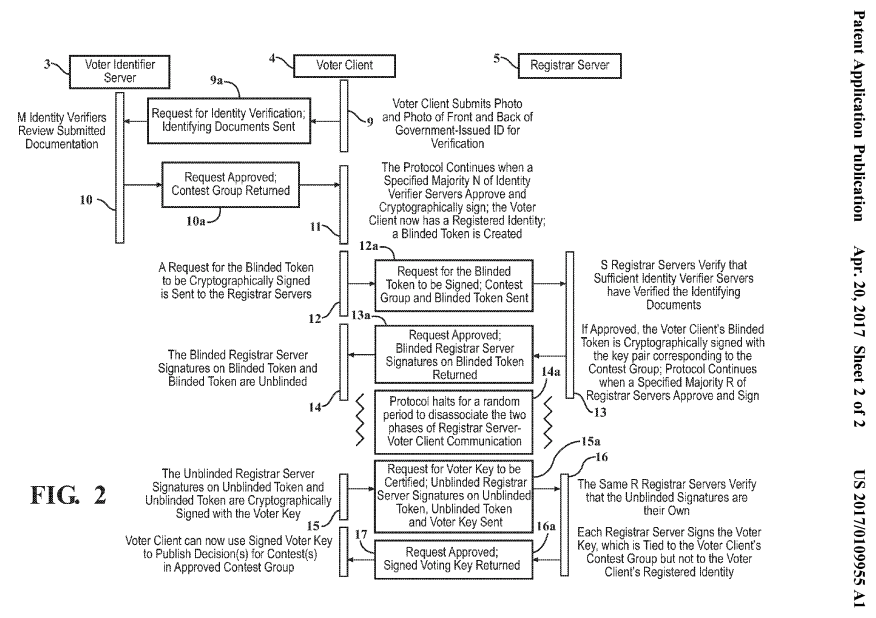
In short, the above figure is the secret sauce with respect to our invention.
Also keep in mind that this powerful protocol could be leveraged outside of the voting space/use case. Another way to interpret the way in which this protocol works is that, based on the identifying information submitted, this person is authorized to do [fill in the blank] anonymously. So, in other words, it could allow someone to submit an identification submission and have a public key anonymously registered to them, which grants them access to something they otherwise wouldn’t have access to, but we digress.
At this point, we’d like to turn your attention to the patent application’s claim language, as it has changed quite a bit over the years, due to shifting from a system and method patent application filing, to simply a method patent application filing. The updated language also more closely reflects the process outlined in Figure 2 above.
AMENDMENTS TO THE CLAIMS – FINAL
The invention claimed is:
1-29. (Cancelled)
- 30. (New) A method comprising:
- generating, by a voter client, a blinded token;
- transmitting, by the voter client to a registrar server, the blinded token;
- receiving, by the voter client from the registrar server, the blinded token, wherein the blinded token comprises a blinded cryptographic signature;
- unblinding, by the voter client, the blinded cryptographic signature of the blinded token;
- unblinding, by the voter client, the blinded token;
- signing, by the voter client, the cryptographic signature of the token with a public key;
- signing, by the voter client, the token with the public key; and
- transmitting, by the voter client to the registrar server:
- (i) the signed cryptographic signature of the token;
- (ii) the signed token; and
- (iii) the public key.
- 31. (New) The method of claim 30, further comprising generating, by the voter client, a public key.
- 32. (New) The method of claim 30:
- wherein the registrar server includes a plurality of remote servers; and
- wherein the steps of the voter client unblinding the blinded cryptographic signature of the blinded token and unblinding the blinded token are performed upon receiving, by the voter client from a number of the remote servers, the blinded token comprising a blinded cryptographic signature of the corresponding remote server.
- 33. (New) The method of claim 30, further comprising halting, by the voter client, for a random period of time before the step of generating, by the voter client, the public key.
- 34. (New) The method of claim 30, further comprising confirming, by the voter client from an election record stored on a blockchain database, the registrar server, before the transmitting, by the voter client to the registrar server, of the blinded token.
- 35. (New) The method of claim 34, wherein the registrar server includes a plurality of remote servers.
- 36. (New) The method of claim 30, further comprising:
- capturing, by the voter client, an identification submission;
- transmitting, by the voter client to an identifier server, the identification submission; and
- receiving, by the voter client from the identifier server, a contest group, wherein the contest group comprises a cryptographic signature of the identifier server.
- 37. (New) The method of claim 36, further comprising:
- confirming, by the voter client from an election record stored on a blockchain database, the identifier server; and
- generating, by the voter client to the blockchain database, a voter client identity including the contest group, wherein the blinded token generated by the voter client comprises the voter client identity.
- 38. (New) The method of claim 37, further comprising:
- upon receipt of the blinded token by the registrar server from the voter client, confirming, by the registrar server from the blockchain database, the voter client identity;
- upon the confirmation by the registrar server of the voter client identity, generating, by the registrar server, the blinded cryptographic signature, wherein the blinded cryptographic signature comprises the contest group; and
- transmitting, by the registrar server to the voter client, the blinded token comprising the blinded cryptographic signature.
- 39. (New) The method of claim 38, wherein the registrar server includes a plurality of remote servers.
- 40. (New) The method of claim 36, further comprising:
- verifying, by the identifier server, an eligibility of the identification submission; and
- upon a determination by the identifier server of the eligibility to be eligible, matching, by the identifier server from an election record stored on a blockchain database, the contest group to the identity submission.
- 41. (New) The method of claim 40, further comprising:
- confirming, by the voter client from the election record stored on the blockchain database, the identifier server; and
- generating, by the voter client to the blockchain database, a voter client identity including the contest group, wherein the blinded token generated by the voter client comprises the voter client identity.
- 42. (New) The method of claim 40:
- wherein the identifier server includes a plurality of remote servers; and
- wherein the step of the voter client generating the blinded token is performed upon receiving, by the voter client from a number of the remote servers, the contest group comprising a cryptographic signature of the corresponding remote server.
- 43. (New) The method of claim 42, further comprising:
- confirming, by the voter client from the election record stored on the blockchain database, the remote servers; and
- generating, by the voter client to the blockchain database, the voter client identity including the contest group, wherein the blinded token generated by the voter client comprises the voter client identity.
- 44. (New) The method of claim 36, further comprising:
- receiving, by the registrar server from the voter client:
- (i) the signed cryptographic signature of the token;
- (ii) the signed token; and
- (iii) the public key;
- confirming, by the registrar server, the contest group of the signed cryptographic signature of the token;
- cryptographically signing, by the registrar server, the public key, wherein the cryptographic signature of the public key comprises the contest group;
- transmitting, by the registrar server to the voter client, the signed public key.
- receiving, by the registrar server from the voter client:
- 45. (New) The method of claim 44, further comprising:
- wherein the registrar server includes a plurality of remote servers; and
- receiving, by the voter client from a number of the remote servers, the signed public key.
- 46. (New) The method of claim 36, further comprising:
- capturing, by the voter client, decisions for the contest group; and
- publishing, by the voter client to a blockchain database, the decisions, wherein the decisions comprise the public key.
While reviewing the patent application, please also take note of and credit the inventor’s of this paradigm shifting innovation that has the real potential to uplift humanity: Adam Ernest (CEO @ Follow My Vote), Nathaniel Hourt (CTO @ Follow My Vote), and Daniel Larimer (CTO @ Block.one).
As a final note with respect to our patent application’s content, we want to be clear that the way in which we’ve described how public key cryptography is leveraged within our system was intentional, although it is a bit atypical of those that have filed for and received cryptography related patents in the past.
To clarify, we specifically refer to signing transactions with a public key throughout our patent application’s content vs a private key. Here’s an explanation from Follow My Vote’s CTO, Nathan Hourt, as to why:
“With regards to the usage of the phraseology “the XYZ transaction is signed with the Voter Public Key,” and similar expressions within the patent application language, this is admittedly an unusual expression of the concept, and this stems in part from the fact that this particular cryptosystem is atypical among asymmetric (or public-key) cryptosystems, and also in part from the way our patent application endeavors to describe the technical processes in high-level, informative language but does not sacrifice accuracy to do so.
First, it is important to examine the unusual properties of the cryptosystem used in our system (and virtually all blockchain systems), namely ECDSA, and distinguish it from most asymmetric cryptosystems (take RSA as an illustrative example). In both ECDSA and RSA, a signature is generated by plugging the message and the private key into a formula, and out of that formula comes the signature. However, the verification process is quite different: in RSA, verification is done by plugging the public key and the signature into a formula, and out of that formula comes the message; however, in ECDSA (our cryptosystem), verification works by plugging in the message and the signature into a formula, and out of that formula comes the public key. This is a critical distinction: RSA and many other asymmetric cryptosystems cannot determine the signer’s identity from the message and signature, they determine the message from the signature and the signer’s identity, but ECDSA determines the signer’s identity from the message and the signature. In light of this, it begins to come clear how the package of the message and the signature could be described as being “signed with the public key” — the public key didn’t do any signing, but the signing embedded it into the message! The message and signature, by nature of the math, come with the public key — it’s just part of the package.
To clarify this meaning, consider a paper contract with a wet-ink signature. We could say “the contract was signed with a pen,” and this would be technically correct, but not particularly informative. We could also say “the contract was signed with the man’s name,” which is also technically correct, but offers a better description of the information conveyed by the signature. In the same way, the patent application says “the transaction signed with the public key,” it is not implied that the public key is the pen that created the signature, but rather that the public key is the information conveyed by the signature. If the patent application said “the transaction signed with the private key,” this would be similar to saying “the contract signed with the pen,” which is technically accurate, but less informative. In the same way as the pen attaches the contractor’s name to the document, the private key attaches the public key to the transaction. It is more informative, then, to say that the message is signed with the public key because this is the useful and relevant information conveyed by the signing, rather than to say that it was signed with the private key, which is not conveyed by the signature but was merely the tool used to make it.
The patent application attempts to clarify how this phrasing is intended in paragraph 0007 by saying “the public key […] signs the transaction, the private key is [used] to authorize the signing” — the public key is the information borne by the signature, but the private key is necessary to authorize one to attach that information to the transaction. It is important to be clear that the public key is the information borne by the signature, as the voter registration process described in FIG. 2 and paragraph 0019 demonstrates that the public key is what is registered to vote, and therefore a transaction with voting decisions must be signed, as per paragraph 0005, with the voter’s public key in order to be recognized as valid. This works because although the private key is necessary to attach the public key to the transaction, the public key is the only information which, like a contractor’s signed name, can be recognized as endorsing the transaction to have effect.
The intended meaning is that the public key is conveyed with the signature, and due to the mechanics of the cryptography, only one who holds the corresponding private key possesses the tool uniquely capable of conveying that particular public key, therefore the message signed with the public key must have come from one who holds the private key, and because the private key is never transmitted, it is extremely difficult for anyone to have the private key except the one who created it, giving the system and its users confidence that the transaction properly signed with a registered public key has the force and effect of the one who registered that public key, even though their specific identity can no longer be recovered.” – Nathaniel Hourt
What does all this mean for Follow My Vote and the voting industry at large?
Follow My Vote has always intended to publish our software as open-source; and, filing a utility patent application for our intellectual property was a strategic move from a defensive perspective.
After speaking with our patent attorney, we’ve come to the conclusion that we’ve done all that we need to do in order to protect ourselves from being sued from practicing our own invention down the line. With this in mind, and in the spirit of the open-source movement, we feel compelled to put our money where our mouth is and abandon our patent application as it exists today.
Moving forward, anyone that wishes to leverage our ideas in their voting system designs can freely do so; and, we hope they do! In other words, what this really means to those competing in the voting space is that these individuals and organizations can now freely innovate on behalf of “We the People” without the impediment of potentially infringing on Follow My Vote’s would-be IP, so that the best ideas can percolate to the top, be tested, and implemented over time.
With our release of this IP, we’re really hoping to spark a new era of innovation in the voting space and foster collaboration between the technology vendors that exist. We also hope to encourage a new wave of potential competitors to enter the voting arena and work toward building secure online voting solutions with true integrity.
For now, we at Follow My Vote have our hands full, as we work to lay the foundation for the development of a secure open-source end-to-end verifiable blockchain-based voting system. But, rest assured that, once we have the opportunity to bring our designs to life, we pledge that we will not attempt to market our solutions for widespread use until they have been battle tested by the brightest tech minds on the planet.
At the end of the day, the world needs to know it’s not about the money for us. Follow My Vote is about solving this global issue for humanity, once and for all, before moving on to the next biggest issue humanity is facing.
We are here to serve the people, plain and simple, and encourage you to follow us on our journey (and perhaps get involved) in the days ahead.
As always, if you are interested in exploring collaboration and/or partnership opportunities, please contact us using the form below:

